교훈
1. 타겟 대기업 사이트가 보유하고 있는 서브 도메인(써드파티)과의 연계 부분을 노려라.
2. 새로 출시되는 사이트의 취약점을 노려라.
우리는 처음에 플래폼을 깊게 찾아봐는데 아무것도 발견 못했다.
그래서 우리는 페북이 소유하고 있는 도메인에 존재하는 minor issue를 노렸다.
첫 이슈는 fb.com 도메인에 존재 하는 써드 파티 서브 도메인에 있었다.
(알아두면 좋은 것 : FB.com은 2010년에 페북에 의해 $8.5M를 획득했다.)
그 서브 도메인은 investor.com 이었고 이슈는 제한된 리다이렉션 이었다.
도메인은 이것처럼 구성 되어 있었다.
이것의 예제로 URL에 위치한 파라미터 값을 바꾸는게 가능했었다.
1
|
이 작은 트릭을 가지고 써드 파티 시스템 (http://shareholder.com/)에 저장된 모든 파일에 리다이렉트가 가능했었다.
심지어 그 방식은 일부 페이크 데이터를 저장하고 그것에 리다이렉트 하는 것도 가능했을 것이다.
또한 이 시스템은 많은 다른 회사들에 의해 사용됬다.
그래서 이 버그는 페북에만 영향을 미치는 것이 아니었다.
적은 위험 이슈로써 페북으로부터 $500를 보상 받았었다.
그러나 소셜엔지니어링 이나 피싱을 함으로써 그것은 더 큰 영향력을 가졌을 지도 모른다.
재밌는건 내친구가 이 시스템에서 또 다른 버그를 발견했다.
그의 관심은 마찬가지로 이 시스템의 취약점에 대해 생각하는 @garagosy 라는 친구에 의해 그려졌다.
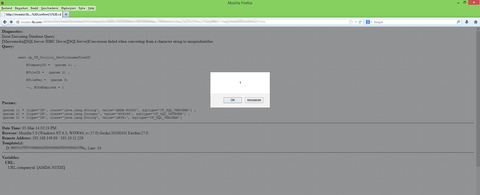
그것은 $500를 보상받은 멋진 XSS다. (화면을 봐라, 파일이름과 user agent가 보인다.)
우리가 저기서 몇가지 놓친 것처럼 보이지만, "sharing is caring (= 좋은 걸 다른 이들에게 공유하다.)".
모든이가 취약점을 발견하기 위해 자신만의 아이디어를 가지고 있다는 것과 버그에 대한 집단지성은 꽤나 효율적이라는 점을 아는 것은 좋은 것이다.
몇주 전에 우리는 페북이 새로운 웹사이트를 출시했고 사람들에게 알렸다는 걸 기사에서 읽었다.
그것은 aconnectedlife.de 인데 우리는 거기서 우연히 두가지 취약점을 발견했다.
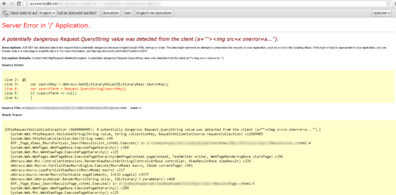
하나는 검색에서 발견된 FPD고 하나는 swf 파일에 있는 XSS다.
두 버그는 $500를 보상받았고 페북 명예의 전당에 올라갔다.
https://en.internetwache.org/facebook-fixes-minor-issues-02-05-2014/
Facebook fixes minor issues
Security is very important at Facebook. As the biggest social network in the world with 1.23 billion members, Facebook has been running a bug bounty program since 2011. Facebook announced they would pay a minimum of $500, with no upper limit. More than $2M has been paid out in rewards, including $1.5M in 2013 alone. As a security researcher you are very proud if you are able to help such a big company, it is also a nice reference and of course the rewards are also quite nice. So at one day we decided that we also want to paticipate in this bug bounty program and looked for vulnerabilities.
We took a deep look at the platform, but were not able to find anything, that might be because Facebook is a very popular target for many whitehat security researchers. But we do not gave up! So we find some nice minor issues on domains which are also owned by facebook.
The first issue was located in a third-party subdomain on the fb.com Domain. (Nice to know: FB.com acquired by Facebook for $8.5M in 2010.) The subdomain: investor.fb.com and the issue was a limited redirection. The domain was structured like this:
It was possible to change the parameters in the URL for example to this:
With this small trick it was possible to redirect to every file which is stored in the third party system of: http://www.shareholder.com/. That way it might even be possible to store some fake data there and redirect to it. This system is also used by many other companies, so this bug does not affect only facebook. It was rewarded by facebook with 500$ as a low risk issue, but with a bit of social engineering or phishing it may have had a bigger impact.
The funny thing is that @smiegles (a whitehat and good friend of us) found another bug in this system. His attention was drawn by @garagosy who thought about a vulnarablitity in the system aswell. It was a cool XSS ((Cross-Site-Scripting) which was rewarded with $500 (via filename and user agent, look at the screen).
It seems like we’ve missed some things there. However, “sharing is caring” and it’s nice to know that everybody has his own ideas to find vulnarablitities and that the crowdsourcing of bugs is quite efficient.
Then a few weeks ago we read in the press that facebook launched a new website to inform people about a smarter / connected world. It is called aconnectedlife.de and we’ve discovered two vulnarablitities there more or less by accident. One FPD (Full-Path-Disclosure) in the search and an XSS (Cross-Site-Scripting) in a swf file. Both bugs were rewarded with $500 and an entry in the Hall of Fame of facebook.com (https://www.facebook.com/whitehat/thanks/)
All in all one could say that the bug bounty program of facebook is quite fair to researchers and also very fast. We are proud that we could help facebook regarding their websecurity and hope that we also will find there some bugs in the future.
Happy hunting! The team of internetwache.org
'버그헌팅 > 방법론' 카테고리의 다른 글
| 안드로이드 정적분석 버그헌팅 검색어 모음 (0) | 2019.03.19 |
|---|---|
| Android Intent필터 XSS 버그헌팅 (0) | 2019.02.28 |
| Bypass firewalls by DNS history (0) | 2019.02.21 |
| Recon 및 해킹 도구 (1) | 2019.02.14 |
| 2019 버그헌팅 책 (0) | 2019.01.03 |